Login SSO ID Essential Steps for a Smooth Single Sign-On Experience

Table of Content
Login SSO ID Everything You Need to Know for Secure Login
Learn How To Access And Manage Your Login Sso Id With Ease. Our Guide Covers Everything From Setup To Troubleshooting, Ensuring A Smooth Sso Experience.
Login SSO ID Essential Steps for a Smooth Single Sign-On Experience
Login SSO ID Keeping track of numerous internet accounts and passwords can be difficult in the modern digital world. By enabling users to log in just once and access numerous apps or services, Single Sign-On (SSO) is a solution meant to streamline this procedure. This comprehensive guide covers all the information you require about Login SSO ID, covering its definition, setup, advantages, and common problems.
What is Login SSO ID?
Register The singular identity utilised in a Single Sign-On system is referred to as an SSO ID. With single sign-on (SSO), users just need to enter their ID and password once to access a variety of apps and services, saving them the trouble of entering their login details every time. By using a single strategy, security is improved, the user experience is streamlined, and there is less need to remember several passwords.
Benefits of Using Login SSO ID
1. Enhanced Convenience
Convenience is a major benefit of Login SSO ID. You may access numerous services with SSO by simply remembering one set of login credentials. It also makes logging in easier and less frustrating to have to remember different passwords.
2. Improved Security
Advanced security features like multi-factor authentication (MFA) and centralised monitoring are frequently included with SSO systems. SSO reduces the possibility of weak or repeated passwords by lowering the number of login credentials a user needs to keep track of. Furthermore, security standards can be uniformly applied to all connected applications thanks to centralised authentication.
3. Streamlined User Experience
By removing the need for frequent log-ins, SSO enables users to seamlessly transition between applications. This efficient method increases productivity while also saving time, particularly in settings where employees must use several platforms or products during the course of the workday.
4. Centralized User Management
SSO provides centralised user management for administrators. This facilitates adding, removing, or updating user access from a single point of management across different systems. Additionally, it streamlines the procedures of onboarding and offboarding users while guaranteeing that access privileges are current.
Services available on SSO Portal Rajasthan
SSO Login Rajasthan (RajSSO) was created to give consumers access to a range of services offered by the Rajasthani government. In order for customers to access various services under SSO Login Rajasthan, the website requests personal data from them.
- GST Home Portal
- Business Registration
- Bhamashah Rojgar Srijan Yojana (BRSY)
- Bhamashah Swasthya Bima Yojana (BSBY)
- Bhamshah Card
- Arms License
- Attendance MIS
- Employment opportunities
- Bank Correspondence
- Change of usage of land
- e-Devasthan
- e-Mitra
- e-Mitra Reports
- e-Learning
- SSO Rajasthan pass
- IFMS-RajSSP
- BPAS -Building plan approval system
 LOGIN SSO ID Update
LOGIN SSO ID UpdateEligibility Criteria for SSO ID Registration
Candidates who wish to apply for the SSO ID (Digital Identity) Registration must meet the following eligibility requirements:-
- The applicant must be a Rajasthani citizen and permanent resident.
- Every Udhyog (Businesses / Industries) in Rajasthan.
- Every State Government Employee (SIPF User)
This idea of a single digital identification for all applications is incredibly creative and helpful. With only one click, it enables all citizens to access a variety of e-services.
How to Set Up Login SSO ID
1. Choose an SSO Provider
SSO provider selection is the first step in configuring the Login SSO ID. There are other choices, including Microsoft Azure Active Directory, OneLogin, and Okta. Determine what you need, then choose a provider with the features and integrations your environment requires.
2. Configure SSO Settings
Configuring the SSO settings is necessary after choosing an SSO provider. Usually, this entails integrating the SSO system with the services and apps you already have. For detailed information on configuring the required settings, such as configuring authentication methods, integrating with your user directory, and setting up the SSO ID, go to the documentation provided by the supplier.
3. Create and Manage User Accounts
You must create and manage user accounts after setting up SSO. In order to do this, user profiles must be created, responsibilities and permissions must be assigned, and each user must have the proper access to the connected apps. you ensure that users can log in and access the necessary services, be sure you test the SSO integration.
4. Implement Security Measures
Use extra security measures like multi-factor authentication (MFA) and strong password policies to optimise the security of your SSO system. In addition to their SSO ID and password, users using MFA must also give a second form of verification, such as a code texted to their mobile device. This provides an additional line of defence against unwanted access.
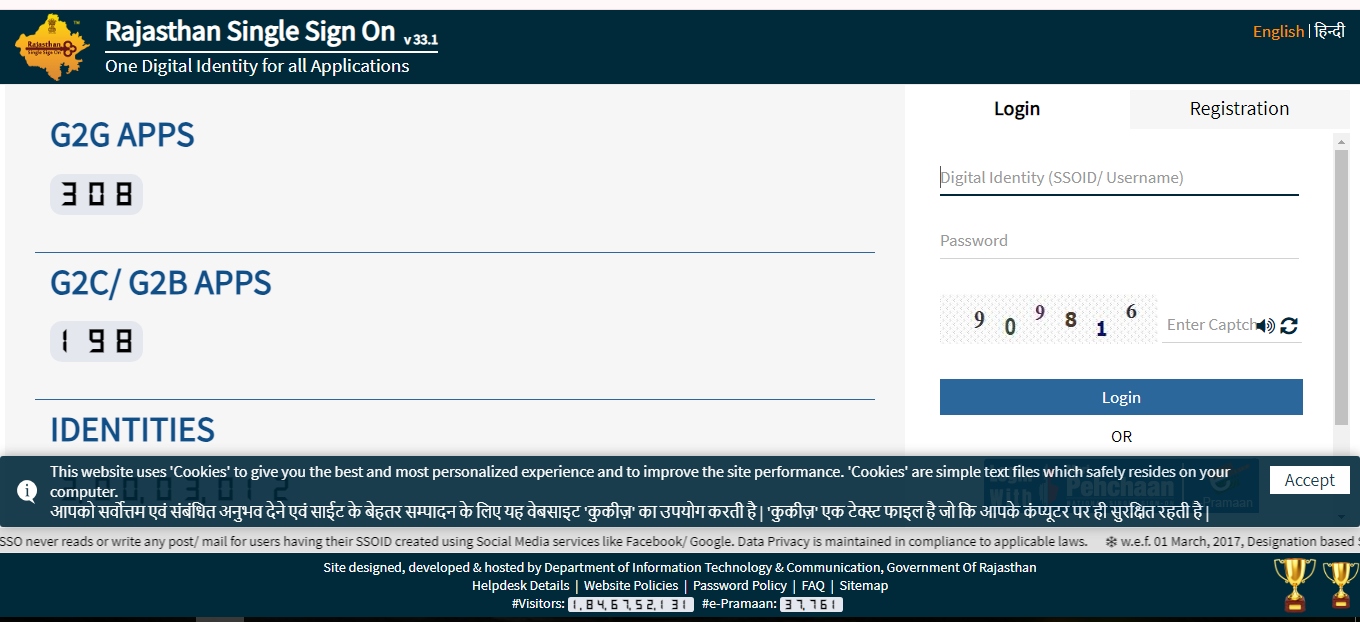 LOGIN SSO ID Apply
LOGIN SSO ID ApplyImplementing SSO ID in Your Organization
Choosing the Right SSO Solution
Take into account the following elements while choosing an SSO solution:
- Make sure the SSO solution is compatible with the systems and apps you already use.
- Features related to security: Keep an eye out for features like MFA, encryption, and industry-standard compliance.
- Scalability: Select a system that can expand to accommodate an increasing number of users as your business does.
- User Experience: Take into account how simple it is for administrators and users to use.
Integration with Existing Systems
SSO integration with your current systems needs to be carefully planned and coordinated. Every application must be configured to function with the SSO system; this is often accomplished by putting one of the supporting protocols (OpenID Connect, SAML, and OAuth) into practice. To make sure the integration works properly and fix any compatibility problems, it must be thoroughly tested.
User Onboarding and Training
In order to implement SSO in your company, people must be trained on the new platform. Give detailed directions on how to utilize the SSO ID and log in. Provide resources or training sessions to users as well so they can learn the advantages of SSO and safe credential management.
Best Practices for SSO ID Management
Secure Password Policies
SSO helps users remember fewer passwords, but it's still important to implement secure password regulations. Promote the usage of complicated passwords that are updated often. To assist users in creating and maintaining safe passwords, think about putting password managers into place.
Multi-Factor Authentication (MFA)
MFA introduces an extra security layer to your SSO setup. Before using an application, users must enter two or more verification factors (such as a password and a code texted to their phone) according to MFA. This aids in preventing unwanted access even in the event that a user's password is stolen.
Monitoring and Auditing
Keep an eye on user activities within the SSO system and conduct regular audits. This makes it easier to spot odd activities, including unsuccessful login attempts or illegal access. Tracking these actions and warning administrators of any security problems can be aided by the implementation of logging and reporting systems.
Access Control and Role Management
Use role-based access control (RBAC) in the SSO system to regulate user permissions. RBAC makes sure users only have access to the resources they require by enabling you to give roles to them based on their responsibilities. Review and update these roles frequently to account for modifications to user duties or organizational structure.
 Login SSO ID Details
Login SSO ID DetailsConclusion
Login SSO ID Implementing an SSO ID system can significantly improve security, streamline user experience, and simplify administration in your organization. By understanding the key features, benefits, and best practices of SSO, you can make informed decisions and successfully integrate this technology into your infrastructure. As the digital landscape evolves, staying updated on emerging trends and technologies will help you continue to optimize your SSO system and enhance your organization's overall security and efficiency.
FAQ (Frequently Asked Questions)
A single set of login credentials can be used to authenticate users across various apps by using an SSO ID, which is a unique identifier found in Single Sign-On systems. By centralizing authentication, it improves security and streamlines the login process.
SSO increases security by minimizing the amount of passwords users need to remember, which facilitates the implementation of multi-factor authentication (MFA) and the enforcement of strong password restrictions. Additionally, it centralizes user authentication, which facilitates access management and monitoring.
OAuth, SAML (Security Assertion Markup Language), and OpenID Connect are the three primary protocols used in SSO. The SSO system and different applications can communicate and authenticate securely thanks to these protocols.
Before integrating SSO, make sure your SSO solution and the applications you wish to incorporate are compatible. Usually, this entails setting up each application to use supported protocols in order to interact with the SSO system. To guarantee a seamless connection, extensive testing is necessary.
A multi-factor authentication (MFA) system requires users to authenticate themselves using two or more methods (such as a password and a code texted to their phone) in order to access certain applications. MFA increases security and makes it more difficult for unauthorized users to log in when combined with SSO.