Azure SSO Integration Guide: Enhance Security with Single Sign-On

Table of Content
Azure SSO Configuration: How to Enable Single Sign-On Easily
Azure Sso Simplifies Secure Cloud Access. Learn How To Implement Single Sign-on, Boost Security, And Optimize Your Enterprise's User Management
Azure SSO Integration Guide: Enhance Security with Single Sign-On
Azure SSO Managing user access to various apps and services can be difficult in the modern digital environment. Businesses are using Single Sign-On (SSO) solutions more frequently in order to improve security and expedite the login process. One of the best SSO options is Azure Single Sign-On (AZURE SSO), which provides smooth interaction with a variety of third-party apps and Microsoft's cloud services. This post will explain AZURE SSO, go over its advantages, explain how to set it up and discuss best practices for making the most of it.
What is Azure SSO?
AZURE SSO is a component of the cloud-based identity and access management service Azure Active Directory (Azure AD). AZURE SSO enables users to access various applications, whether they are hybrid, on-premises, or cloud-based, with just one sign-in. This lowers the possibility of security breaches and does away with the necessity for several passwords.
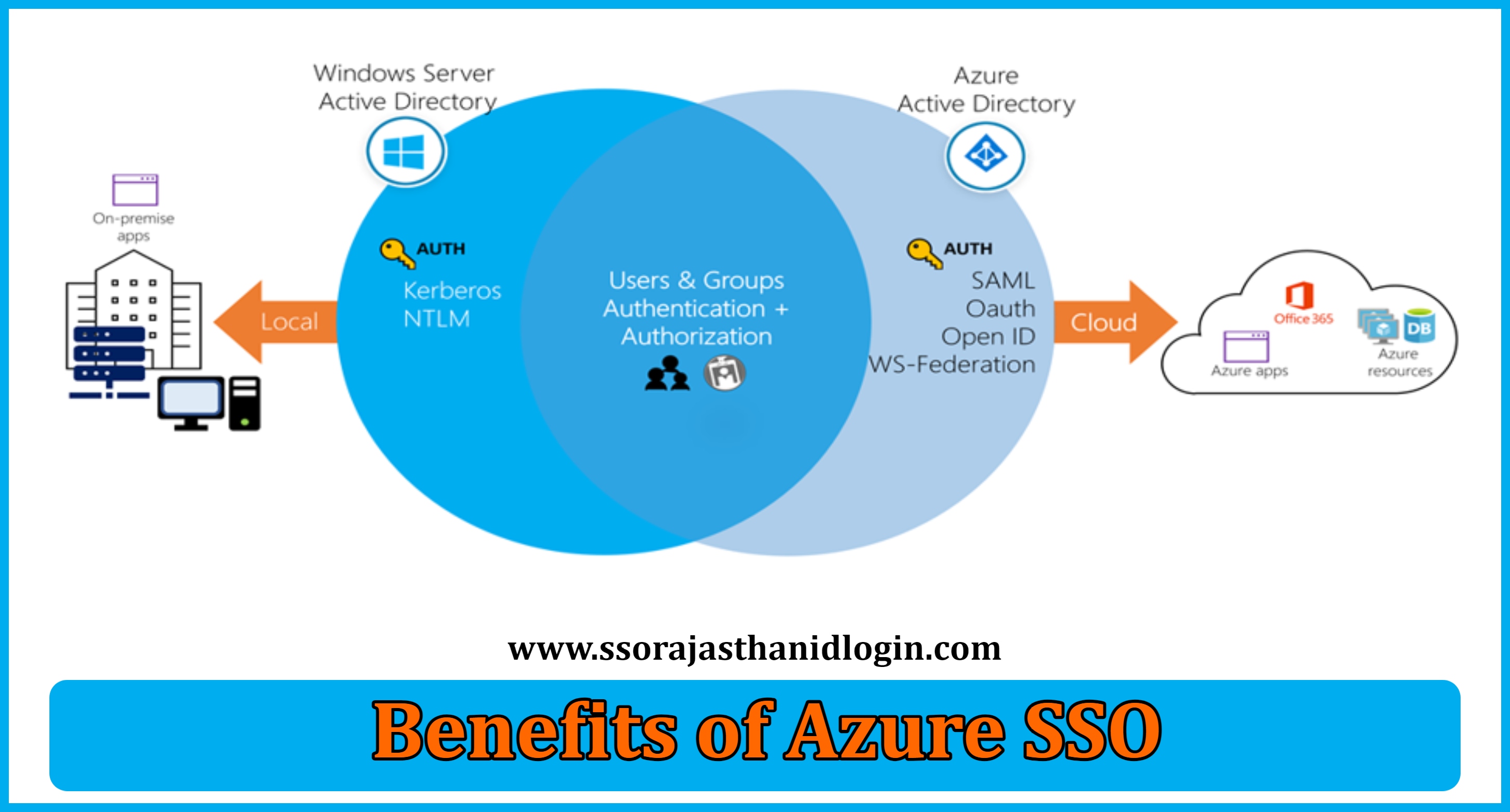
Benefits of Azure SSO
1. Simplified User Experience
Users can access numerous apps with just one login thanks to AZURE SSO, which increases productivity and lessens the hassle of having to remember various passwords. This is especially helpful for large companies whose staff members require daily access to a variety of programs.
2. Enhanced Security
AZURE SSO facilitates the implementation of robust security rules by centralising authentication. To guarantee that only authorised users may access sensitive information, it offers threat detection, conditional access controls, and multi-factor authentication (MFA).
3. Reduced IT Overhead
By reducing the number of requests for password resets and streamlining user management, AZURE SSO lightens the burden on IT teams. IT departments can streamline the onboarding and offboarding procedures by centrally managing user access and permissions.
4. Seamless Integration
Many thousands of well-known on-premises and cloud applications can be seamlessly integrated with AZURE SSO. It is an adaptable solution for companies of all sizes because it incorporates numerous apps, such as Salesforce, ServiceNow, Microsoft 365, and many more.
 AZURE SSO Benefits
AZURE SSO BenefitsHow Azure SSO Works
The foundation of Azure SSO is federated authentication, in which applications receive authentication tokens from Azure AD when user credentials are validated by Azure AD. This is a streamlined procedure:
- User Login: The user enters their login information to access Azure AD.
- Token Issuance: Azure AD provides an authentication token for users.
- Token Presentation: The authentication token is given to the program when the user tries to access it.
- Access Permitted: In the event that the token is legitimate, the application verifies it using Azure AD and permits access.
Setting Up Azure SSO
Step 1: Sign in to the Azure Portal
Enrolling in the Azure Portal with an administrator-level account is the first step towards configuring Azure SSO.
Step 2: Configure Azure AD
- Open Azure Active Directory by navigating: Navigate to the portal's Azure AD area.
- Include a Request: To add the app you wish to link with SSO, select "Enterprise applications" and click "New application".
- Choose a Pre-Configured Application: You can add a custom application or select from thousands of pre-built applications.
 AZURE SSO Login
AZURE SSO LoginStep 3: Set Up SSO for the Application
- Set Up SSO Preferences: Select the SSO protocol that the application supports, either OAuth, SAML, or OpenID Connect.
- Fill out the application details: Give the necessary setup information, including the Identifier and SSO URL.
- SSO Configuration Test: Before deploying SSO to users, utilise the "Test" option to make sure everything is operating as it should.
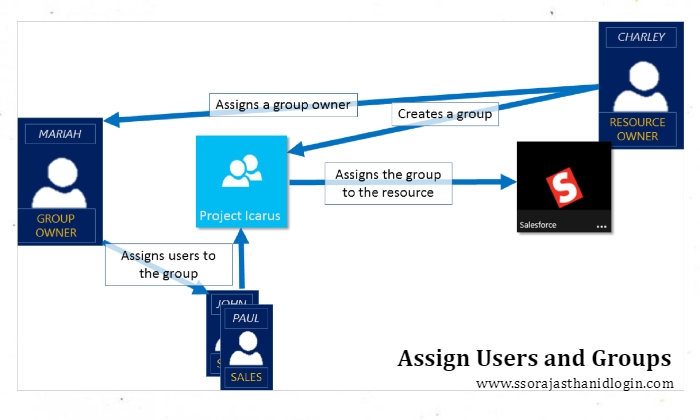
Step 4: Assign Users and Groups
- Assign Access: In the program settings, locate the "Users and groups" area and designate the relevant users or groups.
- Examine & Verify: Examine the assignment and make sure the setup is finished.
Step 5: Monitor and Manage
- Track Usage: To keep an eye on SSO usage and address any problems, use the Azure portal.
- Manage Access: Make necessary updates to configuration and user access settings.
 AZURE SSO Details
AZURE SSO DetailsAzure SSO Integration Methods
Depending on the application, AZURE SSO offers multiple integration techniques. These include:
- SAML (Security Assertion Markup Language): Security Assertion Markup Language, or SAML, is widely used for web-based services and enables parties to exchange authorisation and authentication information.
- OAuth 2.0: An authorisation protocol that lets other apps access user data without disclosing login credentials.
- OpenID: OpenID Connect is an identity layer that sits atop OAuth 2.0 and enables apps to validate user identities and retrieve fundamental profile data.
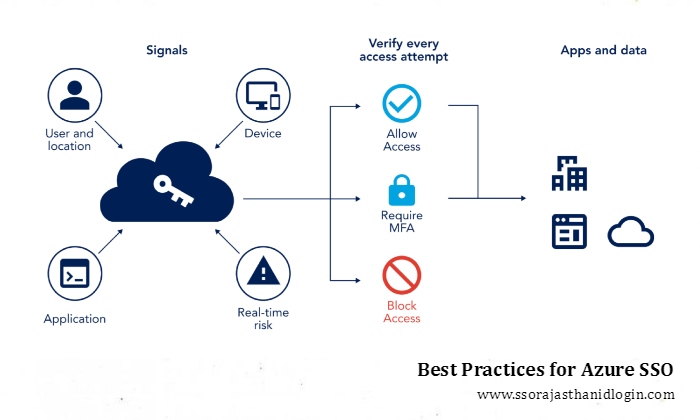
Best Practices for Azure SSO
- Employ Strong Authentication Techniques: To further secure the SSO process, use multi-factor authentication (MFA).
- Examine Access Permissions Frequently: Make sure that only people with permission can access sensitive applications by reviewing and updating user access on a regular basis.
- Put Role-Based Access Control (RBAC) into Practice: To improve the efficiency and security of access management, utilise RBAC to manage permissions according to user roles.
- Maintain Updating Applications: Update and patch integrated apps frequently to guard against security flaws.
- Keep an eye on and audit logs: Keep an eye out for any unusual activity or unauthorised access attempts by regularly monitoring login activity and auditing records.
 AZURE SSO Best Practices
AZURE SSO Best PracticesTroubleshooting Common Issues
- SSO Login Errors: Ensure that the application is properly linked with Azure AD and that the SSO setup parameters are right.
- Token Expiry Issues: Make sure that the token lifetime is properly configured and that users are not experiencing token expiration problems on a regular basis.
- Issues with User Provisioning: Verify that the right people and groups are able to access the application by checking the user assignment settings.
- Connectivity Issues: Verify that neither the Azure AD nor the integrated application are experiencing any network or connectivity problems.
Conclusion
AZURE SSO is a powerful tool that enhances security and simplifies user management by consolidating access across multiple applications into a single sign-on experience. By following the steps outlined in this guide and adhering to best practices, organizations can effectively implement AZURE SSO, streamline access management, and improve both security and user satisfaction.
FAQ (Frequently Asked Questions)
The Microsoft Azure Active Directory (Azure AD) feature known as Azure Single Sign-On (SSO) enables users to log in just once and access numerous applications without having to enter their credentials again. It makes authentication easier for a variety of on-premises and cloud apps.
In response, Azure SSO improves security by minimising the amount of passwords users have to know and keep track of, which reduces the possibility of weak or frequently used passwords. To better safeguard user accounts, it also supports multi-factor authentication (MFA) and other cutting-edge security measures.
The answer is that a large variety of applications, including on-premises apps, custom apps, and cloud-based apps (like Office 365 and Salesforce), can be integrated with Azure SSO. It is compatible with multiple authentication methods, such as OpenID Connect, OAuth, and SAML.
In the Azure portal, log in, select "Enterprise applications," and add a new application to configure Azure SSO. Select from pre-made apps or create your own. Assign users or groups, configure the SSO settings in accordance with the application's specifications, and test the configuration to make sure everything functions as it should.
In response, it is possible to leverage Azure SSO with on-premises apps via federation utilising Active Directory Federation Services (ADFS) or Azure AD Application Proxy. An effortless SSO experience in both on-premises and cloud environments is made possible by this configuration.
If users are having trouble logging in, make sure that the SSO setup settings are accurate and that the users have been granted the appropriate permissions. Examine the network and connectivity for any problems, and look for any error messages in the logs. Updates or troubleshooting of the application or Azure AD settings can also be necessary.